The average cyber attack now takes just 62 minutes to move laterally across an enterprise network. In that brief window, an adversary can escalate from a single compromised endpoint to your crown jewels—customer data, intellectual property, financial systems. The question isn’t whether you’ll face a breach, but whether your network architecture will contain it or become your downfall.
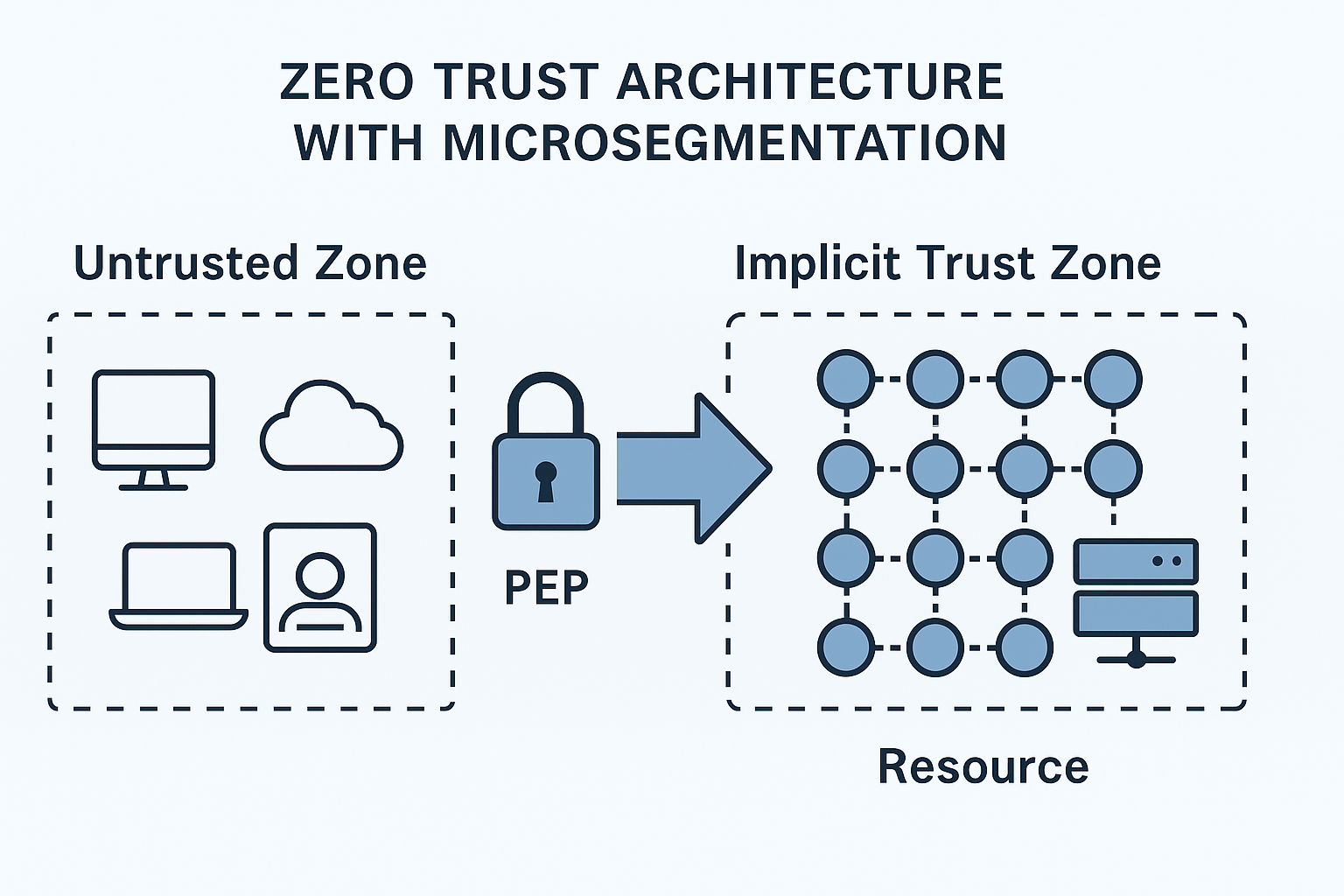
This stark reality has prompted NIST to fundamentally rethink enterprise network security. The emergence of microservices-based applications, geographic spread of IT resources, and access to multiple cloud services have significantly altered the enterprise network landscape, creating new vulnerabilities that traditional perimeter defenses simply cannot address. The answer lies in microsegmentation—a strategic approach that NIST has codified in Special Publication 800-215 as essential for modern enterprise security.
The Adversary’s Advantage: Why Traditional Networks Fail
Today’s cyber adversary operates with surgical precision. They understand that once inside your network perimeter, most organizations offer them a highway to critical assets. Traditional network architectures operate on an implicit trust model—if you’re inside the network, you can communicate freely with other systems. This “castle and moat” approach creates what security professionals call “east-west” vulnerability, where attackers move horizontally through your infrastructure undetected.
The numbers tell the story. Microsegmentation implementations typically achieve 90% reduction in potential breach impact by limiting lateral movement and containing attacks to small network segments. Conversely, organizations without proper segmentation see attackers dwell undetected for an average of 277 days, systematically mapping networks and exfiltrating data.
Modern adversaries leverage this architectural weakness through several sophisticated techniques:
Living off the Land: Rather than deploying malware, attackers use legitimate administrative tools already present in your environment. PowerShell, Windows Management Instrumentation, and legitimate remote access tools become weapons in skilled hands. These tactics generate minimal security alerts because they appear as normal administrative activity.
Credential Harvesting: Once established on a single system, attackers focus on credential theft. They extract cached passwords, exploit service accounts with excessive privileges, and abuse trust relationships between systems. Each compromised credential expands their sphere of access exponentially.
Supply Chain Infiltration: Adversaries increasingly target third-party vendors, managed service providers, and software supply chains. These attacks grant them legitimate access credentials and trusted network pathways, bypassing traditional detection mechanisms entirely.
The sophistication level continues to escalate. In 2024, social engineering, cloud intrusions, and malware-free techniques surged, and nation-state actors intensified cyber espionage and added AI to their arsenal. Your network architecture must evolve to match this threat landscape or risk becoming another statistic.
NIST’s Microsegmentation Framework: Building Defensive Depth
NIST SP 800-215 presents microsegmentation not as a technology product but as an architectural philosophy. The framework recognizes that modern enterprise networks require granular security controls that operate at the application, user, and data flow level rather than traditional network boundaries.
The core principle is simple: assume breach, limit impact. Instead of focusing solely on preventing intrusion, microsegmentation accepts that attackers will occasionally succeed in gaining initial access. The goal shifts to containing that access within the smallest possible network segment while maintaining business functionality.
NIST’s approach centers on three fundamental components:
Identity-Based Access Control: Every network communication request must be authenticated and authorized based on the requesting entity’s identity—whether that’s a user, device, application, or service. This extends zero-trust principles deep into network communications, eliminating the assumption that being “inside” the network grants automatic trust.
Application-Aware Policies: Traditional network security operates at Layer 3 and 4, making decisions based on IP addresses and ports. Microsegmentation operates at Layer 7, understanding application context and implementing policies based on specific application functions and data sensitivity levels.
Dynamic Policy Enforcement: Static network rules become obsolete in environments where applications, users, and threats constantly evolve. NIST emphasizes policy engines that adapt automatically based on changing risk profiles, user behavior, and threat intelligence feeds.
The framework addresses several critical implementation areas:
East-West Traffic Inspection: While most organizations monitor north-south traffic (entering and leaving the network), lateral movement occurs primarily in east-west communications between internal systems. NIST guidelines mandate comprehensive visibility and control over all internal communications.
Cloud and Hybrid Environment Integration: Modern enterprises operate across multiple cloud providers, on-premises data centers, and edge locations. The framework provides guidance for maintaining consistent security policies across these diverse environments without creating operational complexity.
Incident Response Integration: Microsegmentation policies must integrate with incident response procedures, enabling rapid isolation of compromised segments while preserving forensic evidence and maintaining business continuity for unaffected systems.
The Strategic Implementation Imperative
The business case for microsegmentation extends far beyond technical security benefits. Organizations implementing comprehensive microsegmentation report significant improvements in compliance posture, operational efficiency, and risk management capabilities.
Compliance and Regulatory Benefits: Regulatory frameworks increasingly require organizations to demonstrate granular control over data access and movement. PCI DSS, HIPAA, GDPR, and emerging privacy regulations all recognize microsegmentation as a key control mechanism. Implementing NIST-aligned microsegmentation simplifies compliance demonstrations and reduces audit complexity.
Operational Visibility: Microsegmentation implementations generate detailed communications logs, providing unprecedented visibility into application dependencies, user behavior patterns, and system interactions. This visibility proves invaluable for change management, capacity planning, and troubleshooting complex application issues.
Third-Party Risk Mitigation: Modern enterprises rely heavily on vendors, contractors, and managed service providers who require network access. Microsegmentation enables granting precise access levels to third parties without exposing broader network resources, significantly reducing supply chain risk.
However, implementation requires careful planning and executive commitment. Organizations that treat microsegmentation as a pure technology deployment inevitably face adoption challenges, user resistance, and incomplete security coverage.
Start with Business-Critical Assets: Begin microsegmentation around your most valuable and vulnerable assets—customer databases, intellectual property repositories, financial systems. This approach delivers immediate risk reduction while building organizational expertise and demonstrating value to stakeholders.
Embrace Iterative Deployment: NIST guidelines emphasize phased implementation, starting with monitoring modes that provide visibility without impacting operations. This approach allows teams to understand traffic patterns, identify application dependencies, and refine policies before enforcement begins.
Integrate with Existing Security Architecture: Microsegmentation works most effectively when integrated with existing security tools—SIEM systems, identity providers, threat intelligence platforms, and incident response procedures. Standalone implementations create security silos that reduce overall effectiveness.
Your Path Forward: From Awareness to Action
The threat landscape will not pause while your organization debates implementation approaches. Every day without proper microsegmentation represents continued exposure to adversaries who understand your network’s vulnerabilities better than you do.
Identity segmentation provides dynamic, granular access controls based on user behavior, device posture, or application identity, preventing privileged account abuse while stopping unauthorized traffic and preventing breach spread after initial compromise. The technology exists, the framework is established, and the business justification is clear.
Your immediate actions should include:
Conduct a Network Communications Assessment: Map your current east-west traffic patterns, identify critical data flows, and document existing trust relationships between systems. This assessment will reveal your current exposure level and inform microsegmentation design decisions.
Evaluate Your Current Security Architecture: Assess whether your existing security tools can support microsegmentation policies or require integration with specialized platforms. Many organizations discover that their current investments can be leveraged more effectively through proper microsegmentation implementation.
Develop Executive Stakeholder Alignment: Microsegmentation success requires commitment from business leaders who understand the strategic value of containing cyber attacks. Present the business case in terms of operational resilience, regulatory compliance, and competitive advantage rather than purely technical benefits.
Establish Implementation Timelines: Create realistic deployment schedules that balance urgency with operational stability. Organizations that rush microsegmentation implementations often face user adoption challenges that undermine long-term success.
The adversaries targeting your organization have already adapted their tactics to exploit traditional network architectures. NIST has provided the blueprint for defensive evolution through comprehensive microsegmentation frameworks. The question is no longer whether microsegmentation is necessary—it’s whether you’ll implement it before or after your next major security incident.
If your organization lacks internal expertise for microsegmentation planning and implementation, engage with trusted security advisors who understand both the technical requirements and business implications. The cost of expert guidance pales in comparison to the potential impact of a successful cyber attack that could have been contained through proper network segmentation.
The choice is yours: continue operating with network architecture that favors the adversary, or implement the defensive depth that gives your organization the advantage in an inevitable confrontation with cyber threats.