Cybersecurity
-
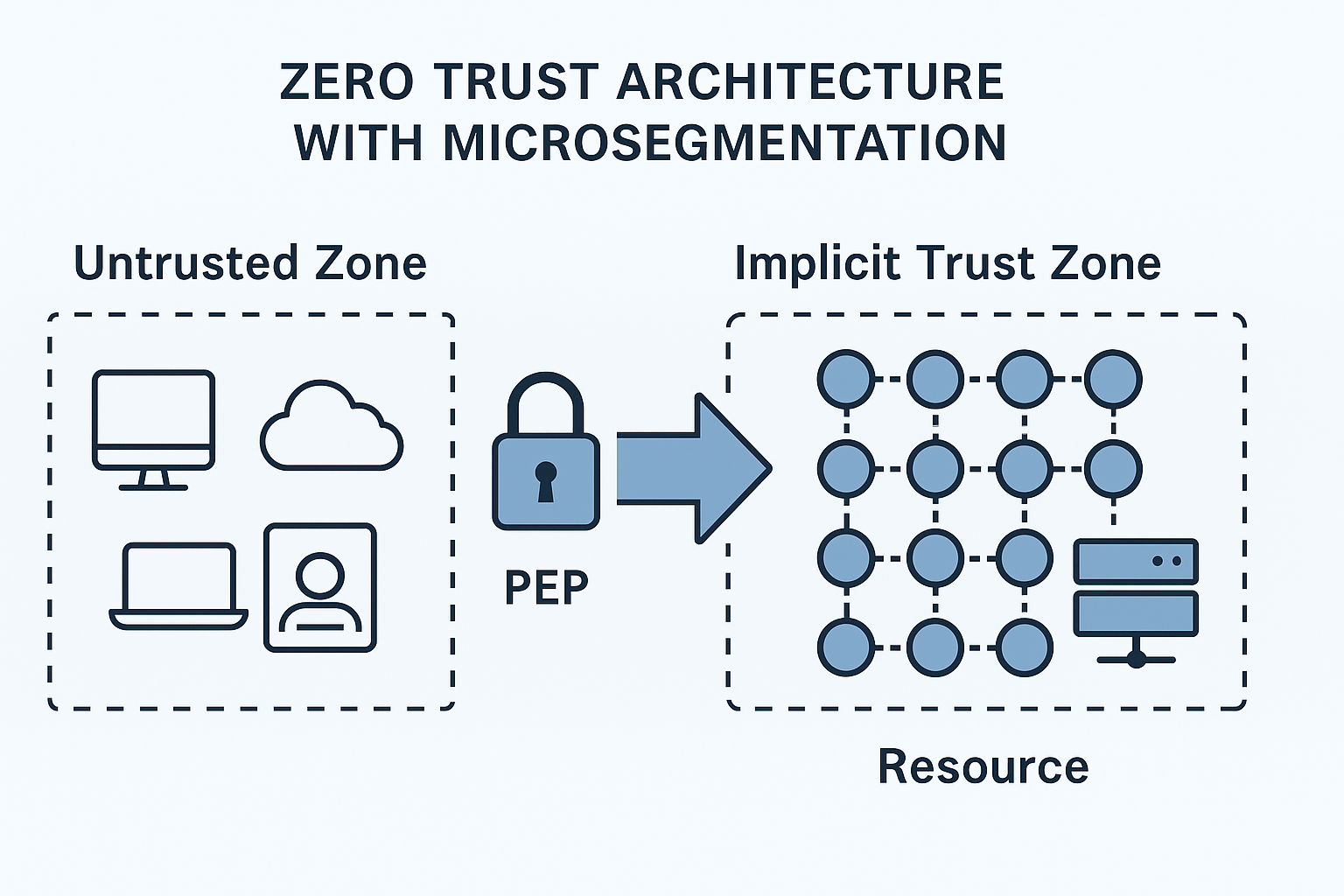
The NIST Microsegmentation Blueprint: Your Shield Against Modern Cyber Attacks
Read more: The NIST Microsegmentation Blueprint: Your Shield Against Modern Cyber AttacksThe average cyber attack now takes just 62 minutes to move laterally across an enterprise network. In that brief window,…
-
Czech cyber agency warns against Chinese tech in critical infrastructure
Source: BleepingComputerRead more: Czech cyber agency warns against Chinese tech in critical infrastructureThe Czech Republic’s NUKIB agency has issued a warning for critical infrastructure organizations to refrain from using Chinese technology or…
-
VirusTotal finds hidden malware phishing campaign in SVG files
Source: BleepingComputerRead more: VirusTotal finds hidden malware phishing campaign in SVG filesVirusTotal has uncovered a phishing campaign utilizing SVG files that mimic Colombia’s judicial system to deliver malware. This method highlights…
-
Patch Tuesday – June 2025
Source: Rapid7 Cybersecurity BlogRead more: Patch Tuesday – June 2025The June 2025 Patch Tuesday update addresses multiple vulnerabilities in Microsoft products, including critical remote code execution flaws.
-
Nexar dashcam video database hacked
Source: MalwarebytesRead more: Nexar dashcam video database hackedThe Nexar dashcam video database has been compromised, leading to potential privacy concerns and data breaches.
-
GOP Cries Censorship Over Spam Filters That Work
Source: Krebs on SecurityRead more: GOP Cries Censorship Over Spam Filters That WorkThe RNC is under scrutiny for allegedly overwhelming individuals with unsolicited donation text messages, raising questions about digital consent and…
-
The Distracted Mind: Why Your Biggest Security Threat Isn’t What You Think It Is
Read more: The Distracted Mind: Why Your Biggest Security Threat Isn’t What You Think It IsResearch highlights that the greatest weakness in cybersecurity isn’t attack sophistication but the human factor. Employee distraction, cognitive overload, and…
-
Kako KPI Metrike Mijenjaju Pravila Igre u Patch Managementu: Putokaz ka Cyber Otpornosti u 2025.
Read more: Kako KPI Metrike Mijenjaju Pravila Igre u Patch Managementu: Putokaz ka Cyber Otpornosti u 2025.This article highlights how ineffective patch management remains one of the biggest enablers of cyberattacks, with unpatched systems causing the…