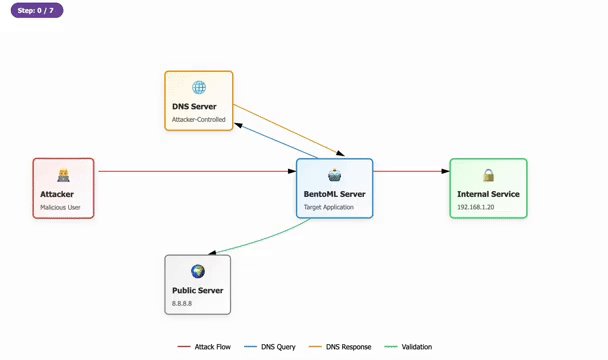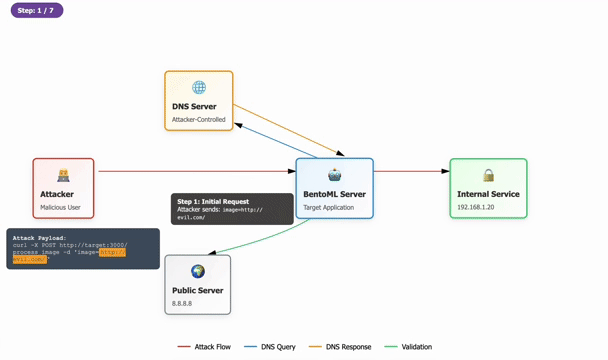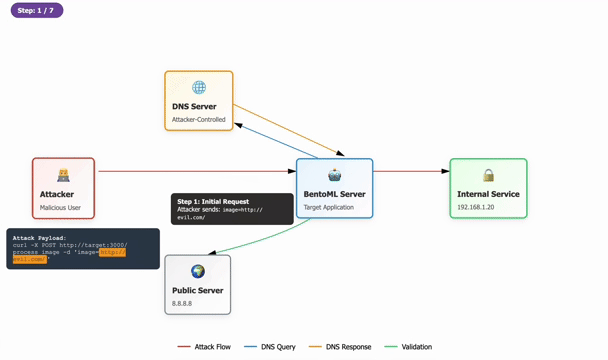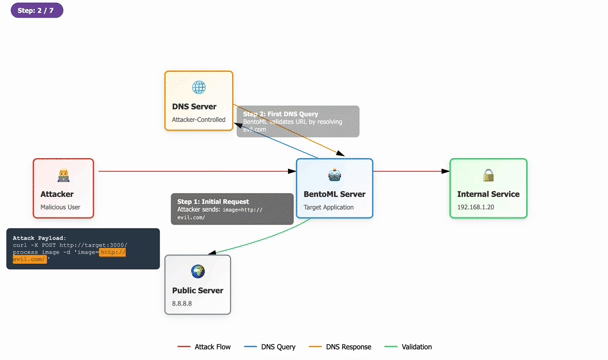
Cybersecurity
-
CISA warns of actively exploited Dassault RCE vulnerability
Source: BleepingComputerRead more: CISA warns of actively exploited Dassault RCE vulnerabilityCISA has issued a warning about a critical remote code execution vulnerability being actively exploited in DELMIA Apriso. This security…
-
Windows 11 23H2 Home and Pro reach end of support in 60 days
Source: BleepingComputerRead more: Windows 11 23H2 Home and Pro reach end of support in 60 daysMicrosoft has announced that the Home and Pro editions of Windows 11 23H2 will cease receiving updates in November. Users…
-
Samsung Fixes Critical Zero-Day CVE-2025-21043 Exploited in Android Attacks
Source: The Hacker NewsRead more: Samsung Fixes Critical Zero-Day CVE-2025-21043 Exploited in Android AttacksSamsung’s recent security update addresses a critical zero-day vulnerability identified as CVE-2025-21043, which has been previously exploited in attacks. This…
-
Apple Warns French Users of Fourth Spyware Campaign in 2025, CERT-FR Confirms
Source: The Hacker NewsRead more: Apple Warns French Users of Fourth Spyware Campaign in 2025, CERT-FR ConfirmsApple has alerted users in France of a spyware threat targeting their devices. This marks the fourth notification this year…
-
In Other News: $900k for XSS Bugs, HybridPetya Malware, Burger King Censors Research
Source: SecurityWeekRead more: In Other News: $900k for XSS Bugs, HybridPetya Malware, Burger King Censors ResearchRecent security news highlights various significant developments, including Huntress research on vulnerabilities and a hefty payout by Google for cloud…
-
The first three things you’ll want during a cyberattack
Source: BleepingComputerRead more: The first three things you’ll want during a cyberattackIn the event of a cyberattack, timely response is vital for mitigation. This article highlights three key factors that can…
-
From Fitbit to financial despair: How one woman lost her life savings and more to a scammer
Source: Malware BytesRead more: From Fitbit to financial despair: How one woman lost her life savings and more to a scammerThis article outlines the harrowing experience of a woman who lost her life savings to a scammer. It highlights how…
-
Cybersecurity Snapshot: Security Lags Cloud and AI Adoption, Tenable Report Finds, as CISA Lays Out Vision for CVE Program’s Future
Source: Tenable ResearchRead more: Cybersecurity Snapshot: Security Lags Cloud and AI Adoption, Tenable Report Finds, as CISA Lays Out Vision for CVE Program’s FutureA recent Tenable report reveals organizations are lagging in securing their AI systems and cloud environments. Despite rapid adoption, the…
-
DELMIA Factory Software Vulnerability Exploited in Attacks
Source: SecurityWeekRead more: DELMIA Factory Software Vulnerability Exploited in AttacksA serious vulnerability has been identified in DELMIA’s factory software, allowing attackers to execute remote code. This exploitation poses significant…
-
Yurei & The Ghost of Open Source Ransomware
Source: Check Point ResearchRead more: Yurei & The Ghost of Open Source RansomwareCheck Point Research has identified a new ransomware group known as Yurei, which has claimed its first victim in September…