Cybersecurity
-
Why Early Visibility Matters: Risk Lurks in the Vulnerability Disclosure Gaps
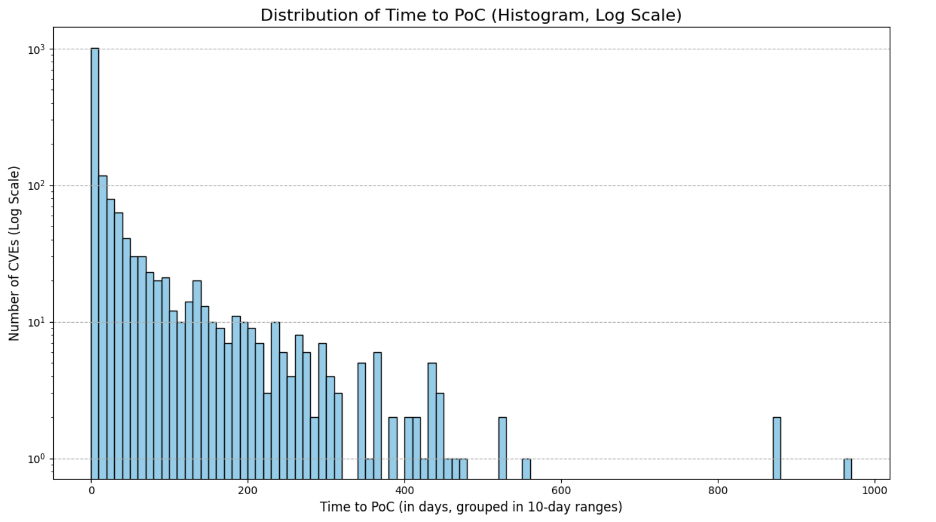
Source: Tenable ResearchRead more: Why Early Visibility Matters: Risk Lurks in the Vulnerability Disclosure GapsRecent analysis reveals significant delays in the vulnerability disclosure process, particularly between public advisories and the National Vulnerabilities Database (NVD).…
-
Why Early Visibility Matters: Risk Lurks in the Vulnerability Disclosure Gaps
Source: Tenable ResearchRead more: Why Early Visibility Matters: Risk Lurks in the Vulnerability Disclosure GapsRecent analysis reveals significant delays in the vulnerability disclosure process, particularly between public advisories and the National Vulnerabilities Database (NVD).…
-
AI is the new UI
Source: CIO MagazineRead more: AI is the new UIThe article discusses how AI is transforming enterprise interactions, creating a seamless relationship between customers and organizations. It emphasizes decision-making…
-
The Download: aluminium’s potential as a zero-carbon fuel, and what’s next for energy storage
Source: MIT Technology Review – AIRead more: The Download: aluminium’s potential as a zero-carbon fuel, and what’s next for energy storageThis edition of The Download discusses aluminium’s potential as a zero-carbon fuel by startup Found Energy and introduces the world’s…
-
ThreatsDay Bulletin: Criminal Exploitation of Weak Points
Source: The Hacker NewsRead more: ThreatsDay Bulletin: Criminal Exploitation of Weak PointsThis ThreatsDay Bulletin discusses how criminals exploit weaknesses in systems, emphasizing the importance of awareness in cybersecurity. It reveals how…
-
Keys to Successfully Managing Cloud and AI Projects and Solving Delays
Source: CIO MagazineRead more: Keys to Successfully Managing Cloud and AI Projects and Solving DelaysOver the past two years, companies have reported a cloud and AI project failure rate three times higher than traditional…
-
Vibe Coding’s Real Problem Isn’t Bugs—It’s Judgment
Source: SecurityWeekRead more: Vibe Coding’s Real Problem Isn’t Bugs—It’s JudgmentResearchers highlight that the integration of security checks into AI coding workflows is crucial. The focus is not just on…
-
Exploitation of Critical Adobe Commerce Flaw Puts Many eCommerce Sites at Risk
Source: SecurityWeekRead more: Exploitation of Critical Adobe Commerce Flaw Puts Many eCommerce Sites at RiskA significant flaw in Adobe Commerce, known as the SessionReaper bug, poses a security threat to numerous eCommerce sites. This…
-
Why Organizations Are Abandoning Static Credentials
Source: The Hacker NewsRead more: Why Organizations Are Abandoning Static CredentialsOrganizations are moving away from static credentials due to the rise of machine identities in cloud environments. This shift is…
-
The web is filling with AI ghosts: Welcome to the machine-shaped web
Source: CIO MagazineRead more: The web is filling with AI ghosts: Welcome to the machine-shaped webThe article explores the evolution of the internet from its early days to the present, emphasizing the role of AI…