Cybersecurity
-
How to Take Vulnerability Management to the Next Level and Supercharge Your Career
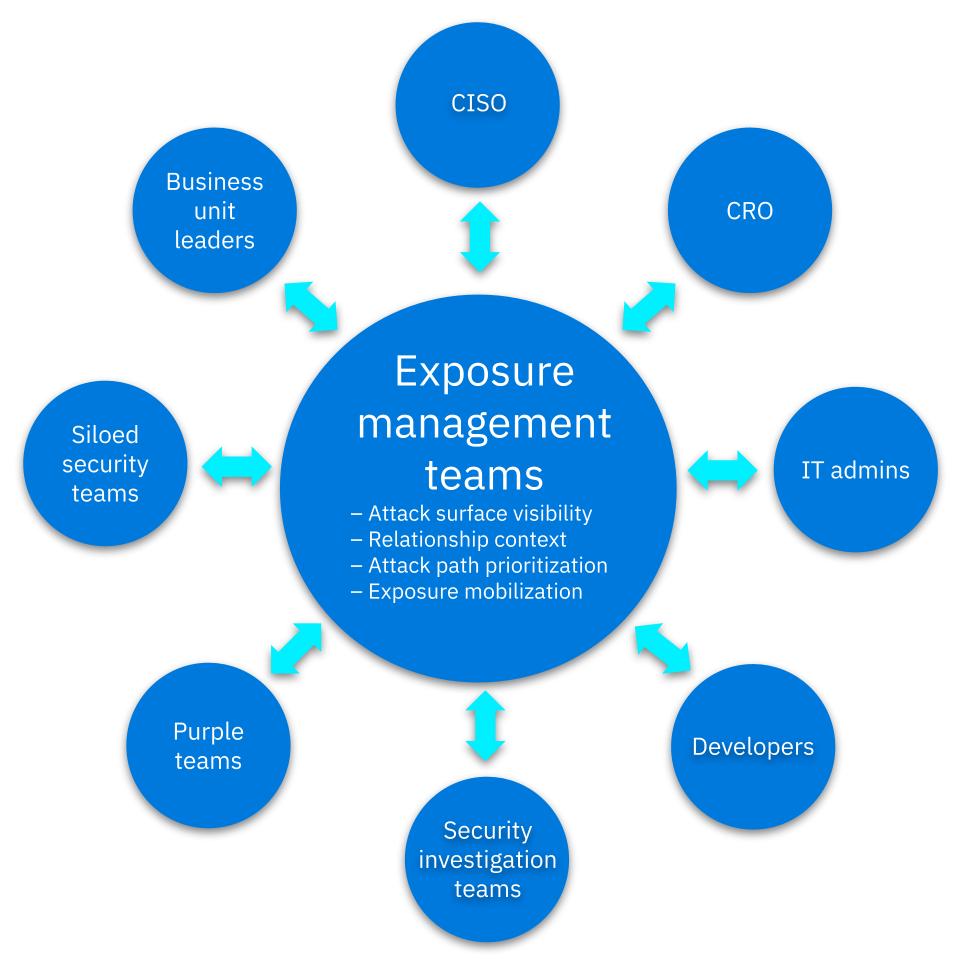
Source: Tenable ResearchRead more: How to Take Vulnerability Management to the Next Level and Supercharge Your CareerThe shift from vulnerability management to exposure management is crucial for cybersecurity leaders. Exposure management enriches insights and improves risk…
-
What Higher Education Do Future IT Leaders and Professionals Need?
Source: CIO MagazineRead more: What Higher Education Do Future IT Leaders and Professionals Need?A LinkedIn study predicts that 68% of the most sought-after jobs in the U.S. did not exist 20 years ago.…
-
New Firefox Extensions Required to Disclose Data Collection Practices
Source: SecurityWeekRead more: New Firefox Extensions Required to Disclose Data Collection PracticesMozilla has announced that all new Firefox extensions must now declare their data collection practices. This requirement is intended to…
-
Year-Old WordPress Plugin Flaws Exploited to Hack Websites
Source: SecurityWeekRead more: Year-Old WordPress Plugin Flaws Exploited to Hack WebsitesRecent reports indicate that critical vulnerabilities in a year-old WordPress plugin are being actively exploited, with approximately 9 million attempts…
-
27th October Threat Intelligence Report
Source: Check Point ResearchRead more: 27th October Threat Intelligence ReportThis report highlights recent cyberattacks, including a data breach at Toys ‘R’ Us Canada and a ransomware attack on Askul.…
-
Ransomware Payments Dropped in Q3 2025: Analysis
Source: SecurityWeekRead more: Ransomware Payments Dropped in Q3 2025: AnalysisA recent analysis by Coveware indicates a decline in ransomware payments during the third quarter of 2025. This trend is…
-
The AI-powered cyber adversary: Staying ahead of a new class of threat
Source: CIO MagazineRead more: The AI-powered cyber adversary: Staying ahead of a new class of threatThis article discusses the emerging threats posed by AI-powered cyber adversaries in cybersecurity. It highlights how attackers are utilizing generative…
-
Why IT projects still fail
Source: CIO MagazineRead more: Why IT projects still failDespite advances in project management methodologies, IT projects continue to face high failure rates. Surveys reveal a significant percentage of…
-
For project strategies to soar, don’t skip those in the middle
Source: CIO MagazineRead more: For project strategies to soar, don’t skip those in the middleMiddle management plays a crucial role in effectively executing business strategy. Without clear understanding and alignment on strategy, projects may…
-
Microsoft ends volume pricing, potentially costing companies millions
Source: CIO MagazineRead more: Microsoft ends volume pricing, potentially costing companies millionsMicrosoft will halt volume discounts for its online services on November 1, creating potential price rises for large enterprises. Industry…