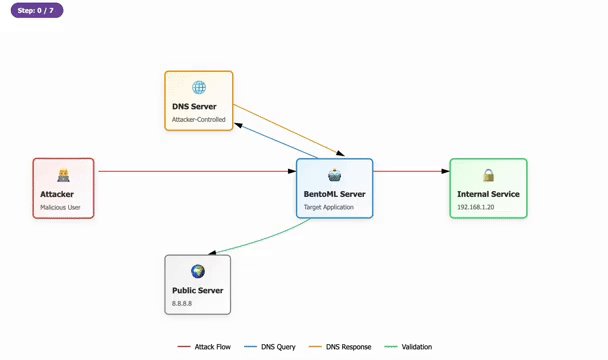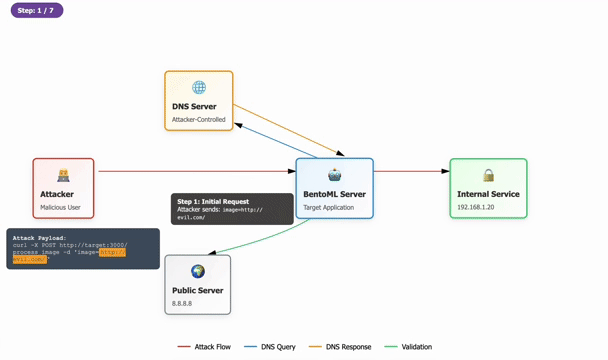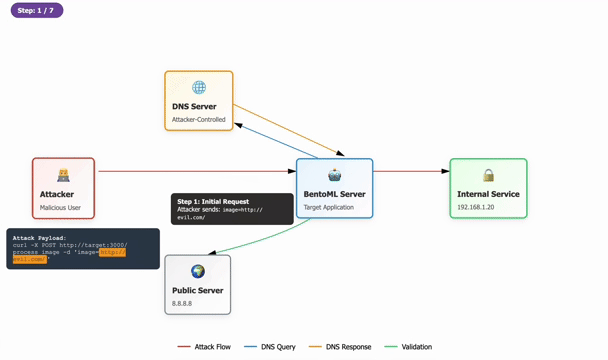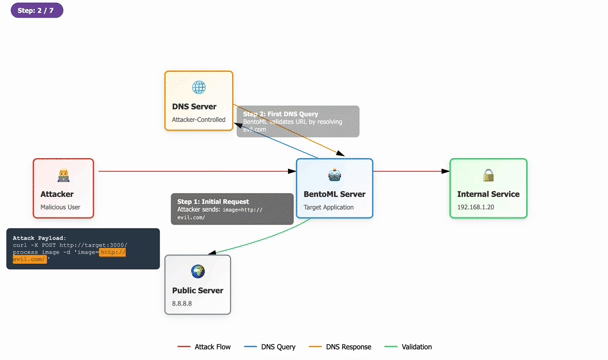
Cybersecurity
-
Shift from Reactive to Proactive: Leveraging Tenable Exposure Management for MSSP Success
Source: Tenable ResearchRead more: Shift from Reactive to Proactive: Leveraging Tenable Exposure Management for MSSP SuccessManaged Security Service Providers (MSSPs) can enhance their cybersecurity offerings by adopting Exposure Management as a Service (EMaaS). This approach…
-
DDoS defender targeted in 1.5 Bpps denial-of-service attack
Source: BleepingComputerRead more: DDoS defender targeted in 1.5 Bpps denial-of-service attackA European DDoS mitigation service has come under attack, experiencing a record-breaking 1.5 billion packets per second. This incident highlights…
-
Wyden calls on FTC to investigate Microsoft for ‘gross cybersecurity negligence’ in protecting critical infrastructure
Source: CyberScoopRead more: Wyden calls on FTC to investigate Microsoft for ‘gross cybersecurity negligence’ in protecting critical infrastructureSenator Ron Wyden criticized Microsoft for allowing default security flaws in its products, which he claims have facilitated ransomware attacks.…
-
China’s ‘Typhoons’ changing the way FBI hunts sophisticated threats
Source: CyberScoopRead more: China’s ‘Typhoons’ changing the way FBI hunts sophisticated threatsTwo major hacking groups have prompted the FBI to change its strategies for identifying advanced cyber threats. A senior FBI…
-
Hackers left empty-handed after massive NPM supply-chain attack
Source: BleepingComputerRead more: Hackers left empty-handed after massive NPM supply-chain attackA massive supply-chain attack affecting the NPM ecosystem has compromised about 10% of cloud environments. Despite the scale of the…
-
Three states team up in investigative sweep of companies flouting data opt-out laws
Source: CyberScoopRead more: Three states team up in investigative sweep of companies flouting data opt-out lawsCalifornia, Colorado, and Connecticut are targeting businesses not complying with data opt-out laws. These states are emphasizing the importance of…
-
Pixel 10 fights AI fakes with new Android photo verification tech
Source: BleepingComputerRead more: Pixel 10 fights AI fakes with new Android photo verification techGoogle’s Pixel 10 leverages C2PA Content Credentials to help users identify genuine images from those altered or created by AI.…
-
Cursor AI editor lets repos “autorun” malicious code on devices
Source: BleepingComputerRead more: Cursor AI editor lets repos “autorun” malicious code on devicesA vulnerability in the Cursor code editor may enable the automatic execution of malicious scripts upon opening certain repositories. This…
-
Chinese APT Deploys EggStreme Fileless Malware to Breach Philippine Military Systems
Source: The Hacker NewsRead more: Chinese APT Deploys EggStreme Fileless Malware to Breach Philippine Military SystemsA Chinese APT group has reportedly compromised a military company in the Philippines using a new fileless malware named EggStreme.…
-
Jaguar Land Rover confirms data theft after recent cyberattack
Source: BleepingComputerRead more: Jaguar Land Rover confirms data theft after recent cyberattackJaguar Land Rover has confirmed that a recent cyberattack resulted in the theft of data. The company was forced to…