Cybersecurity
-
Website Tampering: The Hidden Threat
Source: CIO MagazineRead more: Website Tampering: The Hidden ThreatWebsite tampering represents a growing cybersecurity threat, often going unnoticed until significant damage occurs. Attackers use various methods, such as…
-
Why MDM is Essential Now: Protecting Companies in the Telework Era
Source: CIO MagazineRead more: Why MDM is Essential Now: Protecting Companies in the Telework EraMobile Device Management (MDM) has become critical for businesses navigating the complexities of telework. It addresses security risks associated with…
-
North Korean Hackers Target European Defense Firms
Source: The Hacker NewsRead more: North Korean Hackers Target European Defense FirmsA new wave of cyberattacks attributed to North Korean hackers is affecting European companies in the defense industry, particularly those…
-
SessionReaper Vulnerability Threatens Magento Stores
Source: Malware BytesRead more: SessionReaper Vulnerability Threatens Magento StoresA new vulnerability named SessionReaper affects Magento and Adobe Commerce platforms, allowing attackers to hijack sessions with CVE-2025-54236. Despite a…
-
Spoofed AI Sidebars Can Trick Atlas and Comet Users
Source: BleepingComputerRead more: Spoofed AI Sidebars Can Trick Atlas and Comet UsersAI sidebar spoofing attacks can mislead users of OpenAI’s Atlas and Perplexity’s Comet browsers into dangerous actions by following fake…
-
AI Sidebar Spoofing Puts ChatGPT Atlas, Perplexity Comet and Other Browsers at Risk
Source: SecurityWeekRead more: AI Sidebar Spoofing Puts ChatGPT Atlas, Perplexity Comet and Other Browsers at RiskSquareX has revealed vulnerabilities in popular AI browser extensions, including ChatGPT and Perplexity Comet. Malicious extensions can impersonate these AI…
-
Dissecting YouTube’s Malware Distribution Network
Source: Check Point ResearchRead more: Dissecting YouTube’s Malware Distribution NetworkCheck Point Research examined a coordinated collection of malicious accounts on YouTube known as the Ghost Network. This network promotes…
-
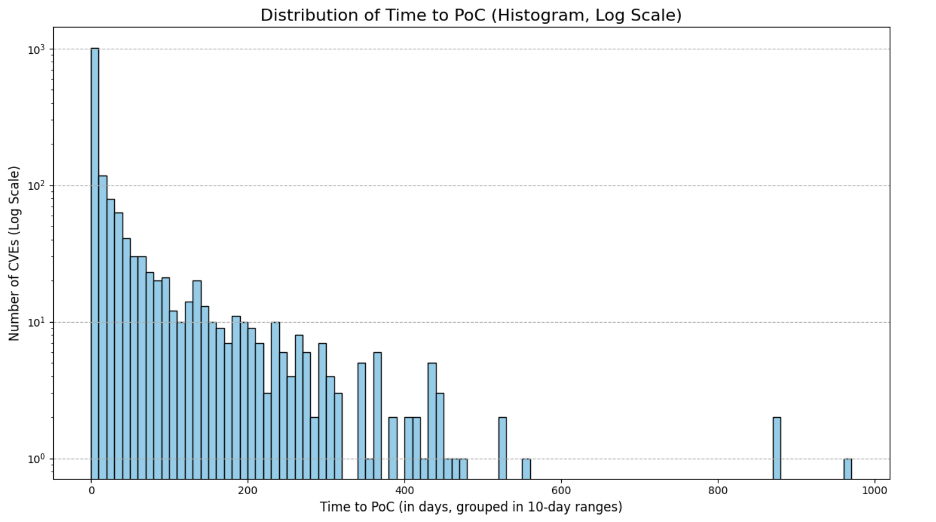
Why Early Visibility Matters: Risk Lurks in the Vulnerability Disclosure Gaps
Source: Tenable ResearchRead more: Why Early Visibility Matters: Risk Lurks in the Vulnerability Disclosure GapsRecent analysis reveals significant delays in the vulnerability disclosure process, particularly between public advisories and the National Vulnerabilities Database (NVD).…
-
Why Early Visibility Matters: Risk Lurks in the Vulnerability Disclosure Gaps
Source: Tenable ResearchRead more: Why Early Visibility Matters: Risk Lurks in the Vulnerability Disclosure GapsRecent analysis reveals significant delays in the vulnerability disclosure process, particularly between public advisories and the National Vulnerabilities Database (NVD).…
-
AI is the new UI
Source: CIO MagazineRead more: AI is the new UIThe article discusses how AI is transforming enterprise interactions, creating a seamless relationship between customers and organizations. It emphasizes decision-making…