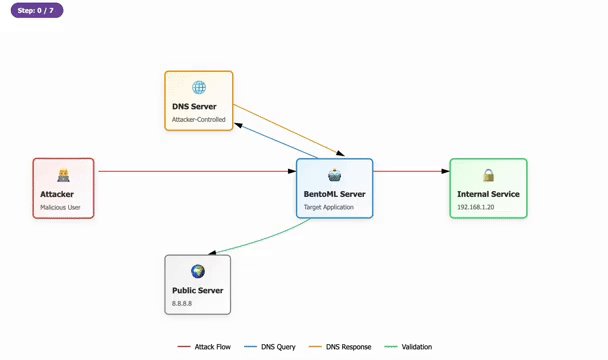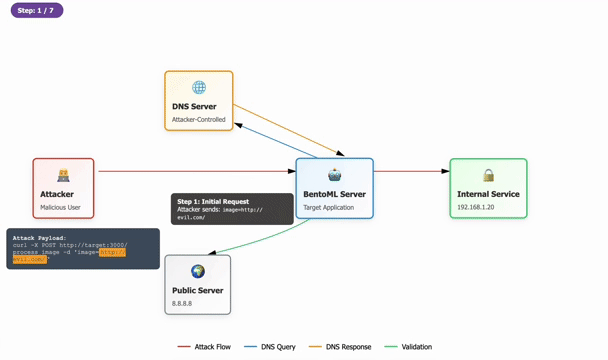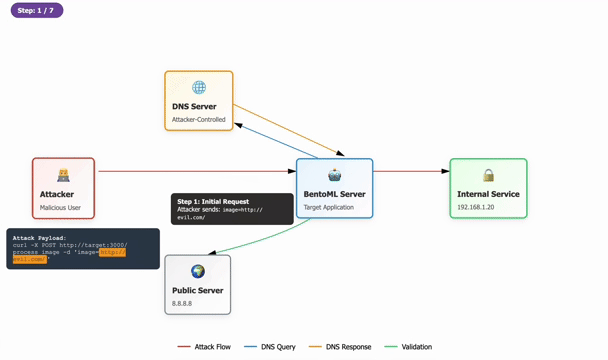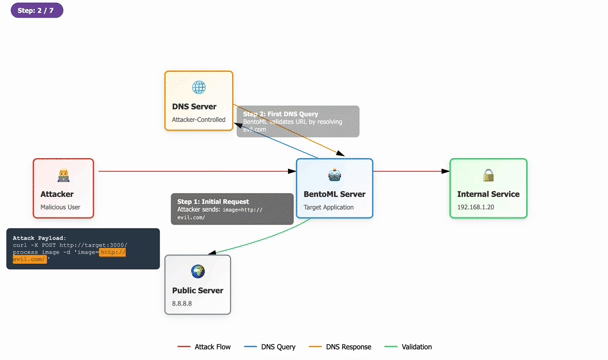
Cybersecurity
-
From Fitbit to financial despair: How one woman lost her life savings and more to a scammer
Source: Malware BytesRead more: From Fitbit to financial despair: How one woman lost her life savings and more to a scammerThis article outlines the harrowing experience of a woman who lost her life savings to a scammer. It highlights how…
-
Cybersecurity Snapshot: Security Lags Cloud and AI Adoption, Tenable Report Finds, as CISA Lays Out Vision for CVE Program’s Future
Source: Tenable ResearchRead more: Cybersecurity Snapshot: Security Lags Cloud and AI Adoption, Tenable Report Finds, as CISA Lays Out Vision for CVE Program’s FutureA recent Tenable report reveals organizations are lagging in securing their AI systems and cloud environments. Despite rapid adoption, the…
-
DELMIA Factory Software Vulnerability Exploited in Attacks
Source: SecurityWeekRead more: DELMIA Factory Software Vulnerability Exploited in AttacksA serious vulnerability has been identified in DELMIA’s factory software, allowing attackers to execute remote code. This exploitation poses significant…
-
Yurei & The Ghost of Open Source Ransomware
Source: Check Point ResearchRead more: Yurei & The Ghost of Open Source RansomwareCheck Point Research has identified a new ransomware group known as Yurei, which has claimed its first victim in September…
-
Apple Sends Fresh Wave of Spyware Notifications to French Users
Source: SecurityWeekRead more: Apple Sends Fresh Wave of Spyware Notifications to French UsersApple has alerted French users about potential spyware targeting them through multiple notifications this year. This continuing effort highlights the…
-
Without Federal Help, Cyber Defense Is Up to the Rest of Us
Source: Dark ReadingRead more: Without Federal Help, Cyber Defense Is Up to the Rest of UsWithout adequate federal support, cybersecurity initiatives may face significant challenges. This article discusses the role of CISA in promoting community-driven…
-
New HybridPetya Ransomware Bypasses UEFI Secure Boot With CVE-2024-7344 Exploit
Source: The Hacker NewsRead more: New HybridPetya Ransomware Bypasses UEFI Secure Boot With CVE-2024-7344 ExploitResearchers have identified a new ransomware variant named HybridPetya that mimics the infamous Petya/NotPetya malware. This strain is capable of…
-
Man gets over 4 years in prison for selling unreleased movies
Source: BleepingComputerRead more: Man gets over 4 years in prison for selling unreleased moviesA Memphis man has been sentenced to 57 months in prison for stealing and selling unreleased movies. He worked at…
-
F5 to Acquire CalypsoAI for $180 Million
Source: SecurityWeekRead more: F5 to Acquire CalypsoAI for $180 MillionF5 is set to acquire CalypsoAI for $180 million to enhance its security offerings. The acquisition will integrate CalypsoAI’s adaptive…
-
Critical CVE-2025-5086 in DELMIA Apriso Actively Exploited, CISA Issues Warning
Source: The Hacker NewsRead more: Critical CVE-2025-5086 in DELMIA Apriso Actively Exploited, CISA Issues WarningA critical vulnerability has been identified in Dassault Systèmes DELMIA Apriso Manufacturing Operations Management software. The flaw, designated CVE-2025-5086, has…